Discovering The Power Of Passkey: Key or Magic Wand?
Understanding the Passkey Essential Roles - Key or Magic Wand?

Discovering the Power of Passkey – Key or Magic Wand?
Google, Microsoft, and other companies have recently introduced the Passkey feature, which will completely replace passwords in the future. The concept of Passkey has created confusion among users, and they do not know what its purpose is and how it works. This quick article helps you understand the concept of Passkey, its purpose and uses, and how to rely on it in the future.
What is Passkey
Discovering the Power of Passkey – Key or Magic Wand?
Passkey is a new method that most companies have begun adopting because it is the most secure. This feature depends on storing various login data (passwords of the PIN type – which you use to unlock your phone -, face print, fingerprint…) in a biometric digital card on the user's device or in an application of a specific company (for example, the Google Chrome application from Google). While registering on a website or logging in with your account, you only need to permit access to the designated Passkey card.
Passkey is based on the WebAuthn standard, which eliminates traditional passwords. You will no longer need a password with Passkey. The most important thing is your biometric information (fingerprint and Face ID), which will be used to log in and register on websites.
To use the PassKey, you must utilize a tool or system based on a specific international classification (defined by the FIDO and WWW Organization). Microsoft, Google, and Apple currently offer the feature of saving passwords via Passkey.
How Does Passkey Work and Is It Safe
Discovering the Power of Passkey – Key or Magic Wand?
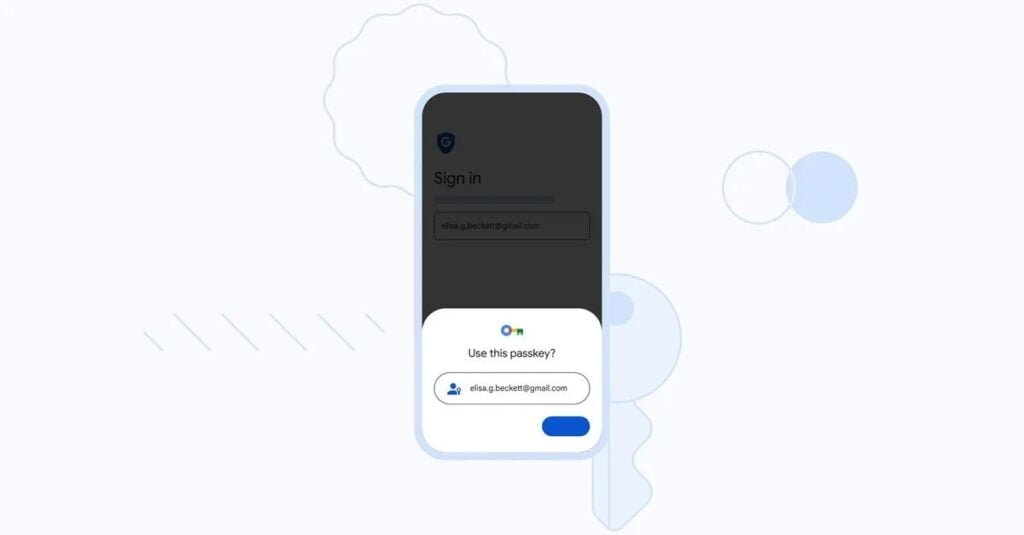
So, how does Passkey work? How can we register on websites and services if there is no password?
To use Passkey, you need – as we mentioned – an intermediary platform that provides the feature, such as Google through its Google Chrome browser (we will rely on this example from now on, but other companies now offer Passkey). You start by creating a Passkey identity in the browser, which includes a set of protection methods: fingerprint, FaceID, and an easy-to-access PIN code. To create your Passkey ID.
This identity is stored in the cloud with Google via two paths: a private path is stored with the company and cannot be accessed. A public path is formed through the private path, including encrypted data generation, which can now be used to register and log into applications and websites.
Assuming that the website has been hacked, all that is leaked is the public path information, which contains information that cannot be used because the original access criteria are stored private.
The current problem with Passkey is that even if Google supports this feature, many other websites and web services still do not. But in the future, it will become something available to users.
It should be noted here that Passkey can use different technologies. For example, at Microsoft, the company aims to convert access to the entire system into Passkey. Using Windows login methods (such as face recognition or fingerprint scanning) is an essential element of Passkey for registering users in system services.
The Purpose of Passkey
Discovering the Power of Passkey – Key or Magic Wand?
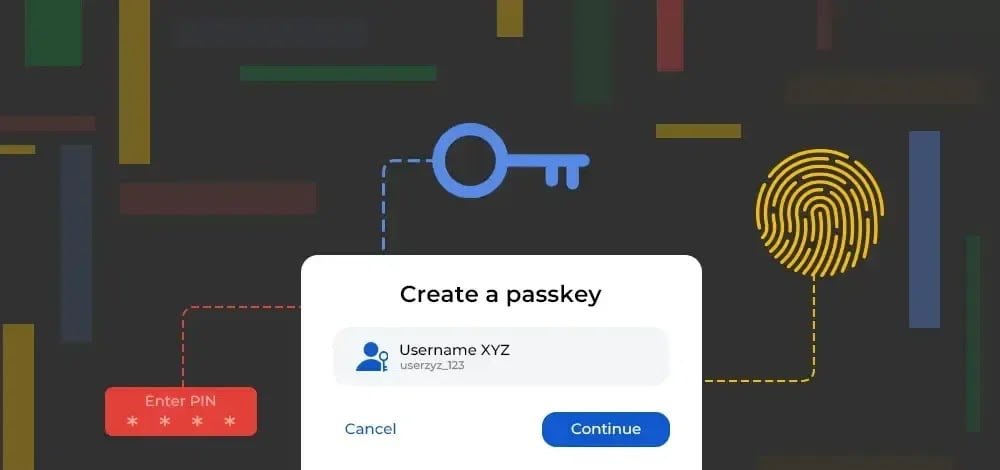
Since time immemorial, privacy and password leaking have been the main concern for users and companies alike. Often, it is the user's mistake to enter passwords on unsafe sites, and companies have to suffer the consequences for the user's negligence. Therefore, I began to devise new ideas to address this problem. The first suggestion was to implement Two-Factor Authentication (2FA), which relies on sending a specific code to the user's email and phone number before granting access to the platform. However, it is not without difficulties and potential issues. What if, for instance, the user loses their phone?
The final and optimal solution that various central companies have reached is the Passkey feature. A feature that essentially eliminates the use of passwords and user names. The best thing that cannot be reused to access user data is biometric data such as fingerprint and face. This makes the possibility of your accounts being hacked much less risky than any other method.
Pros and Cons of Passkey
Discovering the Power of Passkey – Key or Magic Wand?
Pros of Passkey
- Easy and quick registration and login to websites.
- You no longer need to remember the password; other methods like fingerprinting will improve.
- No one can access your accounts even after the site or private data is hacked.
- Easier and the latest standard in digital security.
Cons of Passkey
- It is still unavailable in all services, websites, applications, and software and will not be generalized until years later.
- You must trust big companies with your biometric data; just thinking about it sounds scary!
How to Start Using Passkey
Discovering the Power of Passkey – Key or Magic Wand?
The use of Passkey varies from one platform to another and from one company to another. Because Google is now the most famous for offering Passkey, using it only requires you to follow Google's instructions:
- From the Google Chrome browser settings – in its latest versions – you can find the Google Passkey option or go directly to the following link (make sure to log in from your mobile phone)
- You will be asked to confirm your account and create a Passkey profile using your email
- You will then be asked to enter your biometric data, namely your fingerprint and FaceID
- Complete the requirements, and a Passkey service will be created linked to your private email
- Now, if there is any service that supports Passkey, you can connect it directly from Chrome or just use your email
FAQs about Passkey
Here are some frequently asked questions about Passkey.
How is a Passkey different from a Password?
While a password is generally a combination of characters a user creates, a Passkey is often generated and provided by a system or administrator. Passkeys are frequently used in specific contexts, such as hotel room access or wireless device pairing.
Can a Passkey be reset or changed?
Yes, Passkeys can often be reset or changed depending on the system. Users may need to follow specific procedures the system administrator or platform outlines to update their Passkey.
Are Passkeys more secure than traditional passwords?
Passkeys can provide enhanced security, especially when randomly generated and regularly updated. However, security depends on the Passkey system's implementation and management.
Can Passkeys be shared or transferred?
Passkeys should be treated with confidentiality. While some systems allow sharing within specified users, it is generally advisable to share Passkeys only if explicitly permitted by the system's security policies.
What should I do if I forget my Passkey?
If you forget your Passkey, the recommended action is to contact the system administrator or follow the designated password recovery process. Systems may have specific procedures in place for Passkey retrieval or reset.
How long is a Passkey valid?
The validity period of a Passkey varies depending on the system. Some Passkeys are permanent, while others may expire after a certain period. Users should be aware of the validity duration and renewal procedures.
Can I use the same Passkey for multiple systems?
It depends on the system's configuration. Some systems may allow a single Passkey for multiple access points, while others require unique Passkeys for each context. Always follow the guidelines provided by the system administrator.
Quick Links
Discovering the Power of Passkey – Key or Magic Wand?
We hope you enjoyed this article. If you did, you might want to check out these other resources:
- Top 10 Programs Every Windows User Should Install
- Microsoft SharePoint – Explore The Future of Teamwork
Final Verdict About Passkey
A passkey is a concise term referring to a secure authentication code or key used to gain access to a particular system, network, or encrypted content. It acts as a digital or alphanumeric identifier that verifies the user's identity and grants permission for entry. Passkeys are commonly employed in various contexts, such as computer security, wireless networks, and encrypted communication. They play a crucial role in safeguarding sensitive information and ensuring that only authorized individuals can access protected resources. Using passkeys enhances overall security measures, helping prevent unauthorized access and protect digital assets from potential threats.


